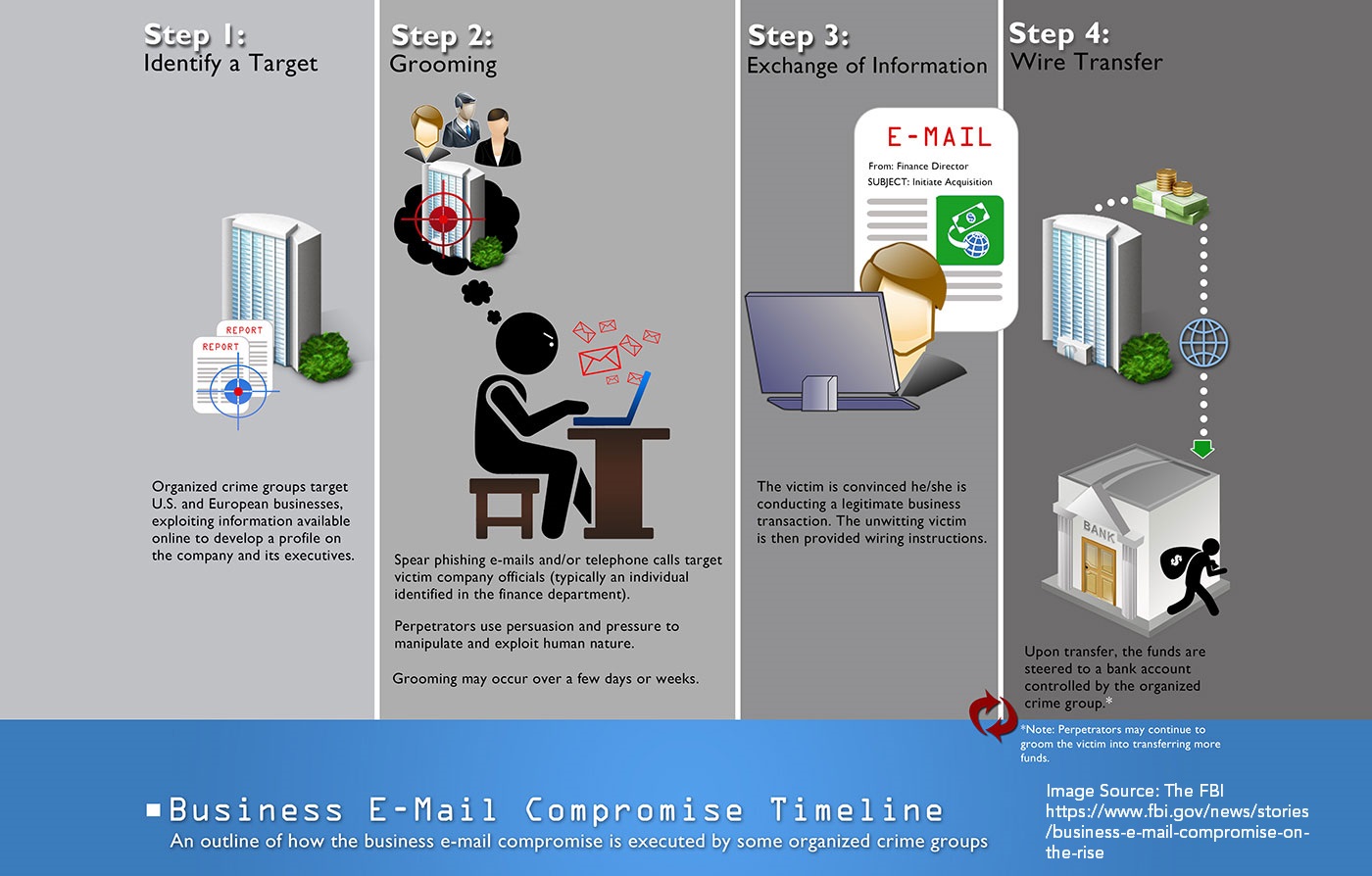
The Dark Web criminals have found a pot of gold and it exists in your email server. Business Email Compromise (BEC) in simple words is the utilization of a company’s emails to create a transaction to direct wire transfer funds from a bank account to an account they control. This can be either domestic or international.
These types of crimes have seen a rapid increase in the last few years. According to the FBI’s internet crime complaint center (IC3), “the BEC scam continues to grow, evolve, and target businesses of all sizes. Since January 2015, there has been a 1,300% increase in identified exposed losses, now totaling over $3 billion.”
What are you doing to minimize the risk this could happen to you?
First of all, you need to assume that some deviate third party is in your email server. Why? Because they’re in all of ours. The use of malware in today’s digital environment is a constant. If you are in receipt of an email directing a financial transaction from within your company it is a mistake to assume it is legitimate.
There are two ways to assure this is a valid request:
- Require verbal confirmation from the party sending the email. Make the phone call prior to executing any transaction to assure the party sending the email did in fact request it AND confirm all of the bank routing and account numbers are correct.
- Possibly require a wet signature on a document including those same routing and account numbers.
A third safe guard is to require the bank to contact you prior to executing any transaction to confirm its legitimacy as well as the account number(s) the transaction is going to.
All of these safe guards will hopefully eliminate the possibility that you will be the victim of a financial crime. Protection is available in the form of an insurance rider to your Cyber or Crime policy to protect the company in the event this crime does occur. Check with a Connor & Gallagher insurance agent to make sure you have this coverage in place.
Written by Tom Connor, Principal at Connor & Gallagher OneSource (CGO)
This blog post is not intended to be exhaustive nor should any discussions or opinions be construed as legal advice - it is intended for educational and/or informational purposes only.
Here are some additional tips, compliments of the FBI:(source https://www.fbi.gov/news/stories/business-e-mail-compromise-on-the-rise)
The Art of Deception
The organized criminal groups that engage in business e-mail compromise scams are extremely sophisticated. Here are some of the online tools they use to target and exploit their victims:
- Spoofing e-mail accounts and websites: Slight variations on legitimate addresses (john.kelly@abccompany.com vs. john.kelley@abccompany.com) fool victims into thinking fake accounts are authentic. The criminals then use a spoofing tool to direct e-mail responses to a different account that they control. The victim thinks he is corresponding with his CEO, but that is not the case.
- Spear-phishing: Bogus e-mails believed to be from a trusted sender prompt victims to reveal confidential information to the BEC perpetrators.
- Malware: Used to infiltrate company networks and gain access to legitimate e-mail threads about billing and invoices. That information is used to make sure the suspicions of an accountant or financial officer aren’t raised when a fraudulent wire transfer is requested. Malware also allows criminals undetected access to a victim’s data, including passwords and financial account information.
If you or your company have been victimized by a BEC scam, it’s important to act quickly. Contact your financial institution immediately and request that they contact the financial institution where the fraudulent transfer was sent. Next, call the FBI, and also file a complaint—regardless of dollar loss—with the FBI’s Internet Crime Complaint Center (IC3).
Don’t Be a Victim
The business e-mail compromise scam has resulted in companies and organizations losing billions of dollars. But as sophisticated as the fraud is, there is an easy solution to thwart it: face-to-face or voice-to-voice communications.
“The best way to avoid being exploited is to verify the authenticity of requests to send money by walking into the CEO’s office or speaking to him or her directly on the phone,” said Special Agent Martin Licciardo. “Don’t rely on e-mail alone.”
Here are other methods businesses have employed to safeguard against BEC:
- Create intrusion detection system rules that flag e-mails with extensions that are similar to company e-mail. For example, legitimate e-mail of abc_company.com would flag fraudulent e-mail of abc-company.com.
- Create an e-mail rule to flag e-mail communications where the “reply” e-mail address is different from the “from” e-mail address shown.
- Color code virtual correspondence so e-mails from employee/internal accounts are one color and e-mails from non-employee/external accounts are another.
- Verify changes in vendor payment location by adding additional two-factor authentication such as having secondary sign-off by company personnel.
- Confirm requests for transfers of funds by using phone verification as part of a two-factor authentication; use previously known numbers, not the numbers provided in the e-mail request.
- Carefully scrutinize all e-mail requests for transfer of funds to determine if the requests are out of the ordinary.






